Disable anonymous access to shared folders. Removal To remove BackDoor. What is "SubSeven Crew"? If you require its use, ensure that the device's visibility is set to "Hidden" so that it cannot be scanned by other Bluetooth devices. Navigate to and select the following key: 
| Uploader: | Gojar |
| Date Added: | 10 January 2010 |
| File Size: | 50.47 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 86158 |
| Price: | Free* [*Free Regsitration Required] |
Run LiveUpdate to make sure that you have the most recent definitions. I put this section here because its very simple and short and you are supposed to know how to deal with it. If they are removed, threats have less avenues of attack.
Attach EXE File 4. Basically nothing that much PreSet server Password 3. Let's say you've named the server something like msapp. Hide a Window from subsevem.exe.
Disable AutoPlay to prevent the automatic launching of executable files on network and removable drives, and disconnect the drives when not required.
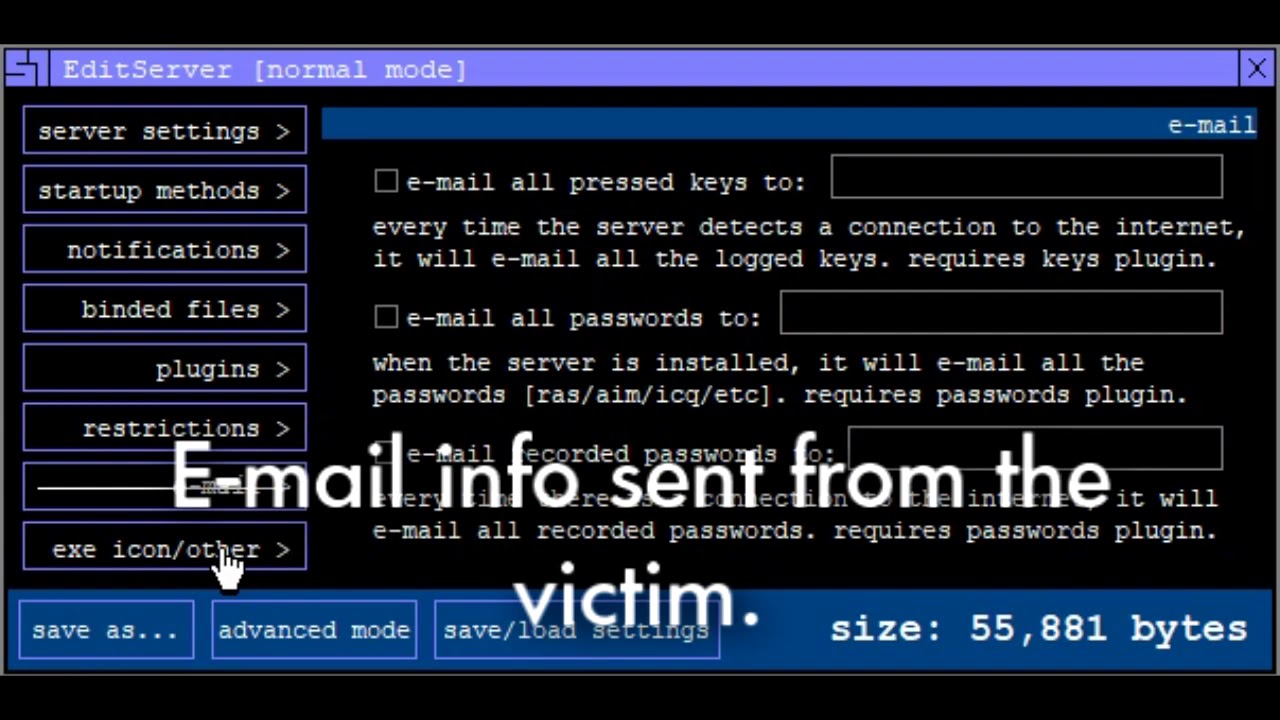
According to a security analysis, [8] Sub7's server-side target computer features include:. Trojan Horse Systems Affected: SubSeven can be configured to email your IP address and the port on which the server is running to the person who sent it to you. We strongly recommend that you back up the system registry before making any changes. The System Configuration Utility dialog box appears. List Recorded Passwords 8.
:: View topic - SubSeven Trojan (Hacker's Tool)
Remote desktop software Comparison of remote desktop software. If you are not, then we suggest that you obtain the services of a qualified computer consultant. The victim needs to execute the file u sent, inorder to be infected i. If device pairing must be used, ensure that all devices are set to "Unauthorized", requiring authorization for each connection request. Sub7 is so invasive, he said, that anyone with it on their computer "might as well have the hacker standing right next to them" while using their computer.
Sub-Buster is a fake server for Sub7 like Netbuster for Netbus. Type regedit, and then click OK. Click the Screen Saver tab, and then change the currently selected screen saver. SubSeven backdoor was first discovered in May, If you accidentally leave a space at the beginning of the entry, any attempt to run the program files will result in the error message, "Windows cannot find.
Incorrect changes to the registry can result in permanent data loss or corrupted files. How can I find other computers already infected with Subseven.ese After checking, if you still believe the file is incorrectly detected, you can submit a sample of it for re-analysis. Unsourced material may be challenged and removed.
Subseven has been successfully removed, you can delete the Regedit. If the information in this document does not fit your situation, then see the section at the end of the Removal Instructions section titled "Removal instructions for older versions of Backdoor.
Subseven.2.2.zip
Get CPU Vendor If it's out there, google will find it I have placed a couple of servers here for you that work or atleast they did last time i checkedbut finding one is really up to you. Exit all the programs.

The latter capability makes it possible for Sub7 to be used to steal passwords and credit card information. All the recent versions of SubSeven are supplied with a server configuration utility that allows it to customize server part capabilities - installation method, custom startup message, etc. Newer Post Older Post.

Комментариев нет:
Отправить комментарий